when we access a website over https, there is always a complex process happen under the hood between your browser and remote websrever to ensure the communicate is secure.

there are some concepts involved before we could explian the whole process
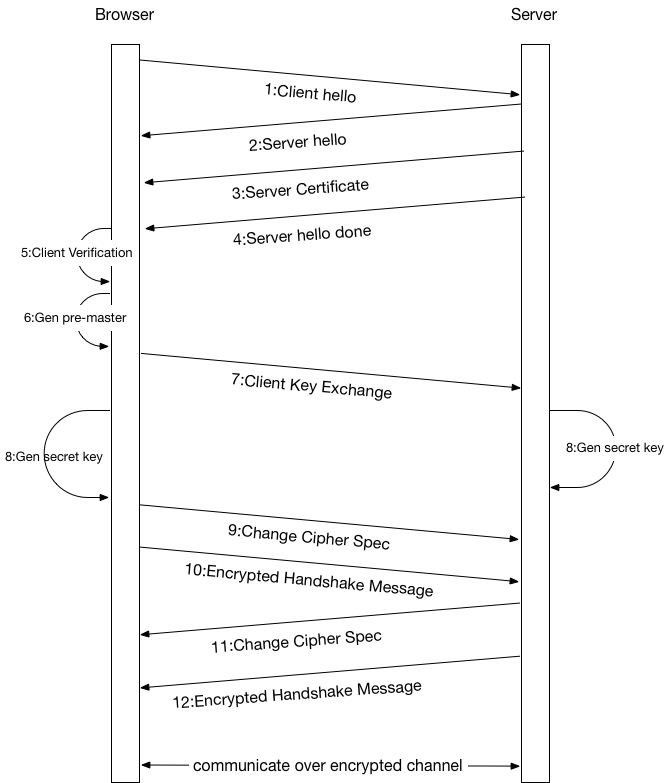
- Client Hello: browser will send out a random number
random1and a list of encryption algorithmsalgosit could understand to server over http. different kind of browsers with different versions could support different encryption algorithms. - Server Hello: server will send out a random number
random2and selected encryption algorithmalgobased onalgosto client over http, the server has determined the client and server will communicate based on encryption algorithmalgogoing forward. - Server Certificate: server will send out it's certificate to client over http, the certificate could be verified by CA to prove it comes from the server.
- Server Hello Done: server will send the
server hello donemsg to client over http to indicate it has no more info - Client Verification: client will use the CA in it's OS to verify server's certificate and extract the public key from the certificate for further usage
- Gen pre-master: client will generate a
pre-master - Client Key Exchange: client could use server's public key to encrypt
pre-masterand send to server, server could use it's private key to decryptpre-master - Gen secret key: now both client and server know
random1(from client),random2(from server) ,pre-master(from client) andalgo(from server), they could generate the symmetric secret key based on the information. - Change Cipher Spec: the client sends the ChangeCipherSpec notification to the server and start the symmetric encryption handshake
- Encrypted Handshake Message: client will send handshake message to server based on
algoand the generated secret key - Change Cipher Spec: the server sends the ChangeCipherSpec notification to the client and start the symmetric encryption handshake
- Encrypted Handshake Message: server will send handshake message to client based on
algoand the generated secret key - Finish: going forward the client and server could both understand the encrypted message based on
algoand the generated secret key so they could communicated over encrypted channel from then on